Introduction:
- A firewall is a network security device or software that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Its primary purpose is to establish a barrier between a secure internal network and untrusted external networks, such as the internet. Firewalls are crucial for preventing unauthorized access, protecting sensitive data, and detecting and blocking malicious activities.
- While firewalls are designed to enhance network security, they are not immune to exploitation.
- To mitigate these exploits, it's essential to regularly update firewall configurations, apply security patches, and employ additional security measures such as intrusion detection and prevention systems. Regular security audits and monitoring can also help identify and address potential vulnerabilities in the firewall setup
Top 7 Firewall Vulnerabilities
While incorporating a firewall into your security strategy is crucial, it's important to acknowledge that firewalls may exhibit vulnerabilities. A firewall vulnerability refers to a mistake in the design, implementation, or configuration of a firewall that could be exploited to compromise the integrity of the trusted network it aims to safeguard. Knowing this, we have categorized firewall exploits into multiple categoriesc focusing solely on the top seven for this module.
Ddos Attack
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the regular functioning of a network, service, or website by overwhelming it with a flood of internet traffic. The primary goal of a DDoS attack is to make the target inaccessible to its intended users by flooding it with an excessive amount of traffic, rendering its resources (such as bandwidth, servers, or other network components) overwhelmed and unable to respond to legitimate requests. Some key characteristics of DDoS attacks include:
Distributed Nature:
DDoS attacks involve a multitude of compromised computers and devices, often forming a network of bots or zombies (a botnet). These devices, controlled by the attacker, collectively generate and direct traffic towards the target.
Overwhelming Traffic:
The attack floods the target with an overwhelming volume of traffic, exceeding its normal capacity to handle requests. This flood of traffic can come in various forms, such as data packets, connection requests, or other network-related activities.
Botnets:
Many DDoS attacks are executed using botnets, which are networks of compromised computers or devices under the control of a single entity (the attacker). These botnets are often built by infecting computers with malware, allowing the attacker to coordinate the attack without the knowledge of the device owners.
Outdated Firewall Software
Outdated firewall software can lead to exploits in several ways, as it may have vulnerabilities that attackers can exploit to bypass security measures or compromise the integrity of the firewall. Some key ways in which outdated firewall software can contribute to security risks are as follows:
Unpatched Vulnerabilities:
Over time, security vulnerabilities are discovered in firewall software, and vendors release patches or updates to address these issues. If the firewall software is not regularly updated, it may contain known vulnerabilities that attackers can exploit to compromise the system.
Failure to Address New Threats:
Cyber threats are continually evolving, and firewall vendors release updates to counter new attack techniques. Outdated firewall software may lack defenses against the latest threats, increasing the risk of successful exploits that take advantage of novel attack vectors.
Inadequate Signature Databases:
Firewalls often use signature-based detection mechanisms to identify known patterns of malicious activity. If the firewall's signature database is not regularly updated, it may not recognize new malware or attack signatures, allowing malicious traffic to pass through undetected.
Lack of Documentation
The lack of documentation regarding firewall configurations and security policies can introduce several challenges and risks, potentially amplifying the impact of firewall exploits.
Configuration Errors:
Without proper documentation, it becomes challenging for administrators to accurately understand and replicate the firewall configurations. This increases the likelihood of configuration errors that could inadvertently expose vulnerabilities or create openings for exploitation.
Delayed Troubleshooting:
When issues arise, whether they are related to performance, connectivity, or security, the lack of documentation hinders efficient troubleshooting. Administrators may struggle to pinpoint the source of problems or understand the intended design of the firewall.
Inconsistent Policy Enforcement:
Documentation serves as a reference for security policies and rules. Without it, there is an increased risk of inconsistent policy enforcement, where different administrators or teams may interpret and implement rules differently, leading to security gaps or unnecessary restrictions.
Insider Attacks
Insider attacks in the context of firewall exploits involve individuals within an organization exploiting their access or knowledge to bypass or manipulate the firewall's security measures. Unlike external attacks that come from outside the organization, insider attacks originate from within, often taking advantage of the trust and privileges granted to individuals within the network.
Unauthorized Access:
An insider with legitimate access to the network may abuse their privileges to gain unauthorized access to restricted areas or resources, potentially bypassing firewall controls.
Configuration Manipulation:
Insiders with knowledge of the firewall's configuration settings might exploit this information to manipulate rules, disable the firewall, or create openings that allow malicious traffic to pass through.
Abuse of Remote Access:
If an insider has remote access privileges, they may misuse this to connect to the network from outside and potentially evade firewall restrictions that are designed to block unauthorized remote access.
Improper Configuration
Improper configuration of a firewall refers to errors or oversights made during the setup and management of the firewall, which can lead to security vulnerabilities and potential exploits.
Incorrect Rule Settings:
If firewall rules are not accurately configured, they may allow unauthorized traffic to pass through or block legitimate traffic. For example, misconfigured rules might inadvertently leave open ports that should be closed or vice versa.
Default Settings:
Some firewalls come with default settings that are not secure for all environments. If these defaults are not adjusted based on the specific needs of the network, they may leave unnecessary services or ports open, creating potential entry points for attackers.
Incomplete Logging and Monitoring:
Inadequate logging and monitoring configurations may result in the firewall missing important events or failing to alert administrators about suspicious activities. This can give attackers the opportunity to go undetected.
Failure to Activate Controls
The failure to activate and enforce proper controls on a firewall can significantly increase the risk of successful firewall exploits. Controls are security measures and configurations implemented to protect the network, and when these controls are not activated or properly enforced, it creates vulnerabilities that attackers may exploit.
Unrestricted Traffic Flow:
In the absence of properly configured rules and restrictions, the firewall may allow unrestricted traffic flow, enabling attackers to send malicious traffic or conduct reconnaissance without detection.
Malware Propagation:
A lack of controls may permit the spread of malware within the network. Malicious actors may exploit vulnerabilities in uncontrolled communication channels, allowing malware to move laterally and compromise multiple systems.
Weak Authentication:
Controls related to user authentication and access management are critical. Failure to activate strong authentication controls may lead to unauthorized individuals gaining access to the firewall's administrative interface.
Basic Inspection Tools
A lack of basic inspection tools in the context of a firewall can significantly hinder the detection and response to firewall exploits. Inspection tools are essential for monitoring and analyzing network traffic, identifying potential security threats, and understanding the effectiveness of the firewall's protective measures.
Limited Visibility:
Basic inspection tools, such as packet analyzers or network monitoring tools, provide visibility into the details of network traffic. Without these tools, security teams have limited visibility into the actual data packets traversing the network, making it challenging to identify suspicious or malicious activities.
Inability to Analyze Traffic Patterns:
Monitoring tools help in analyzing network traffic patterns, detecting anomalies, and identifying potential signs of an exploit or attack. The absence of such tools makes it difficult to recognize unusual patterns that may indicate a security incident.
Failure to Identify Exploited Vulnerabilities:
Inspection tools are crucial for identifying vulnerabilities in networked systems. Without them, security teams may be unaware of exploited vulnerabilities, making it difficult to address the root cause of the exploit.
Types of Firewall Attacks
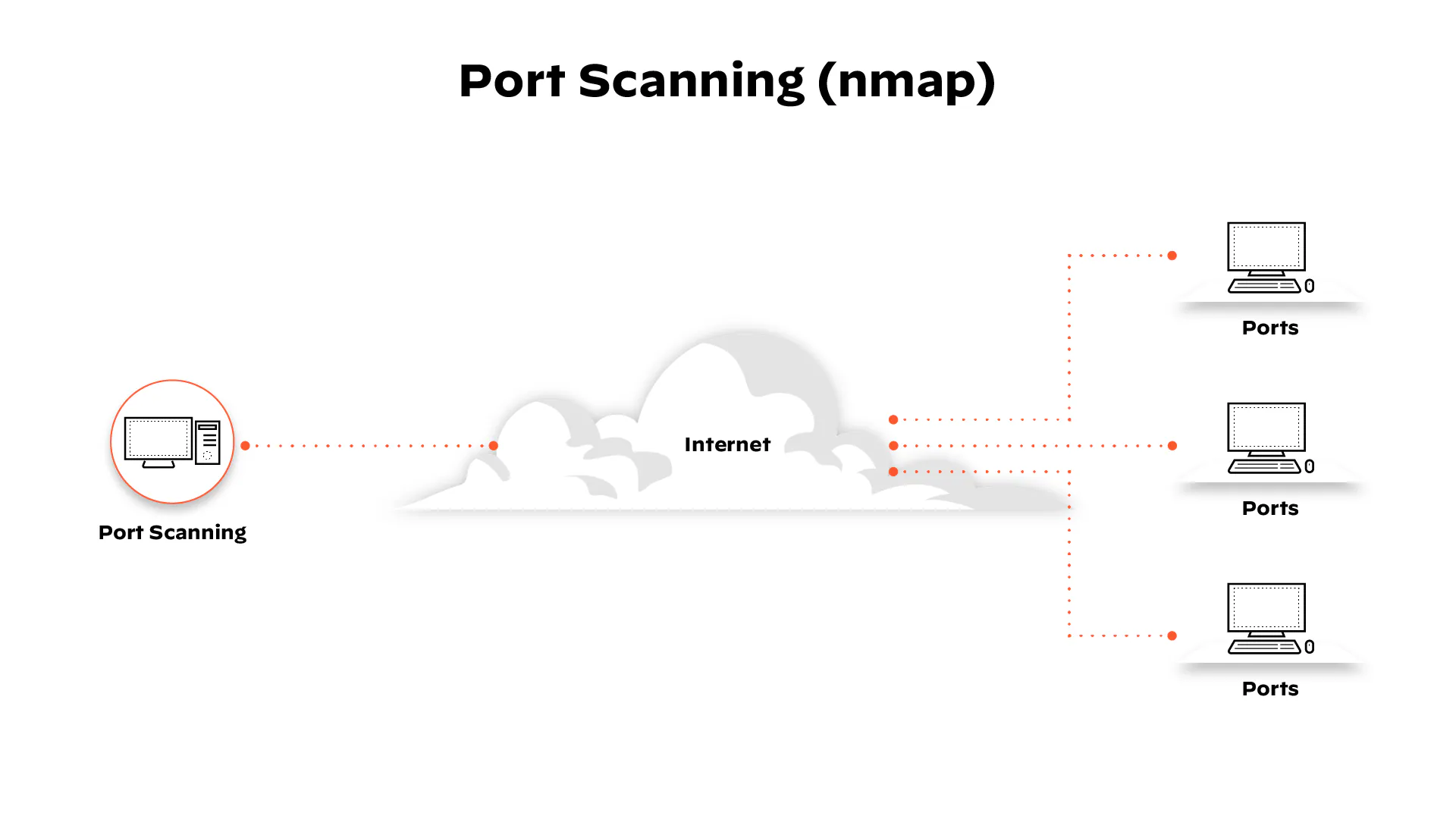
Port Scan
To target a computer, an unauthorized user must ascertain the accessible TCP or UDP ports, which
correspond to specific services and programs. Each program interacting with the Internet or
accepting connections is allocated an IP port number ranging from 0 to 65536. These port numbers
typically indicate a particular type of service; for instance, SMTP commonly uses port 25 for
Internet email, while port 110 is employed for POP. When downloading files from an FTP site,
your computer utilizes either port 20 or port 21.
Intruders often conduct scans on victim computers, probing multiple ports to identify active
ones. Once open ports are identified, intruders or their malicious software narrow down future
attacks to a specific port type. Given that it's uncommon for a remote computer to connect to
numerous ports simultaneously, firewalls are designed to detect such activities.
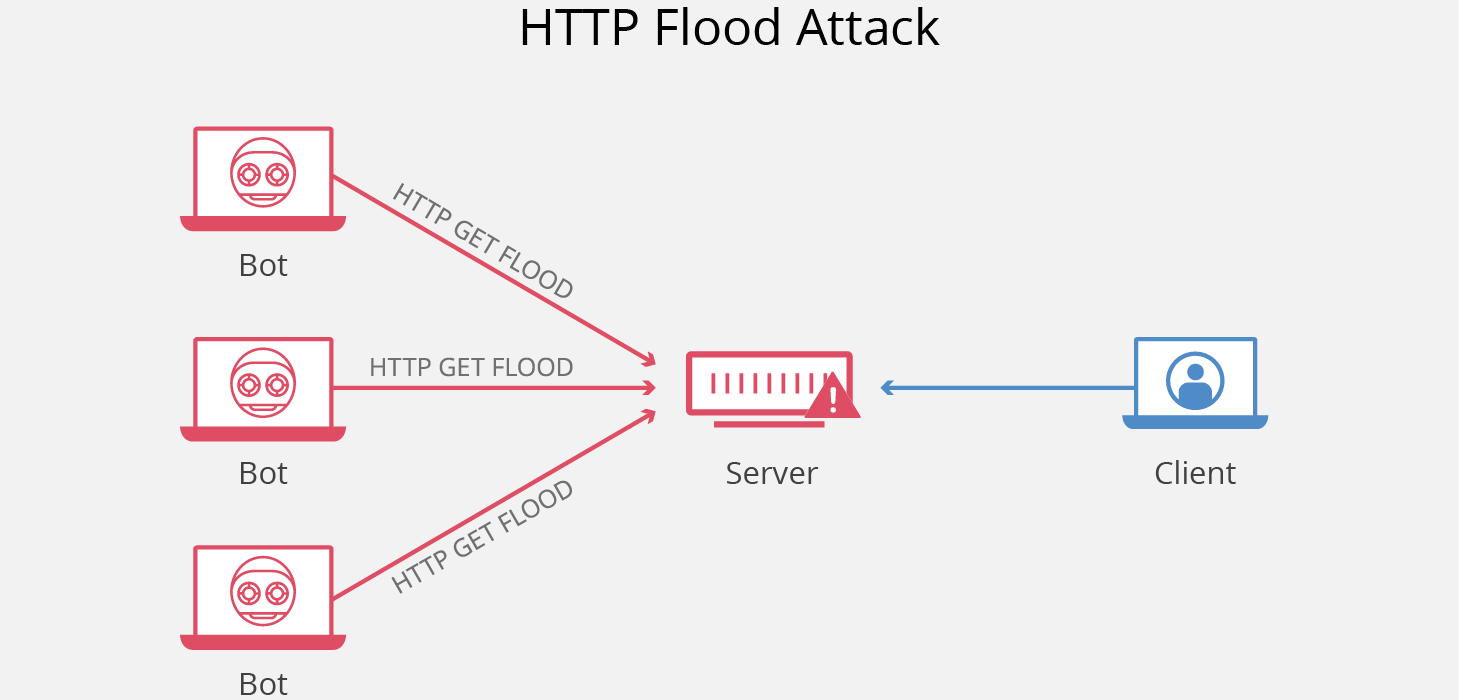
Network Traffic Flood
The fundamental idea behind network traffic deluge attacks is that an excess of something positive can be harmful. Rather than trying to pinpoint a computer's vulnerabilities, specialized programs known as flooders send a substantial volume of legitimate network packets to a single PC, aiming to overpower its response capacity. This often leads to a Denial of Service (DoS) attack, with flooders successfully bypassing firewalls and taking control of targeted PCs.
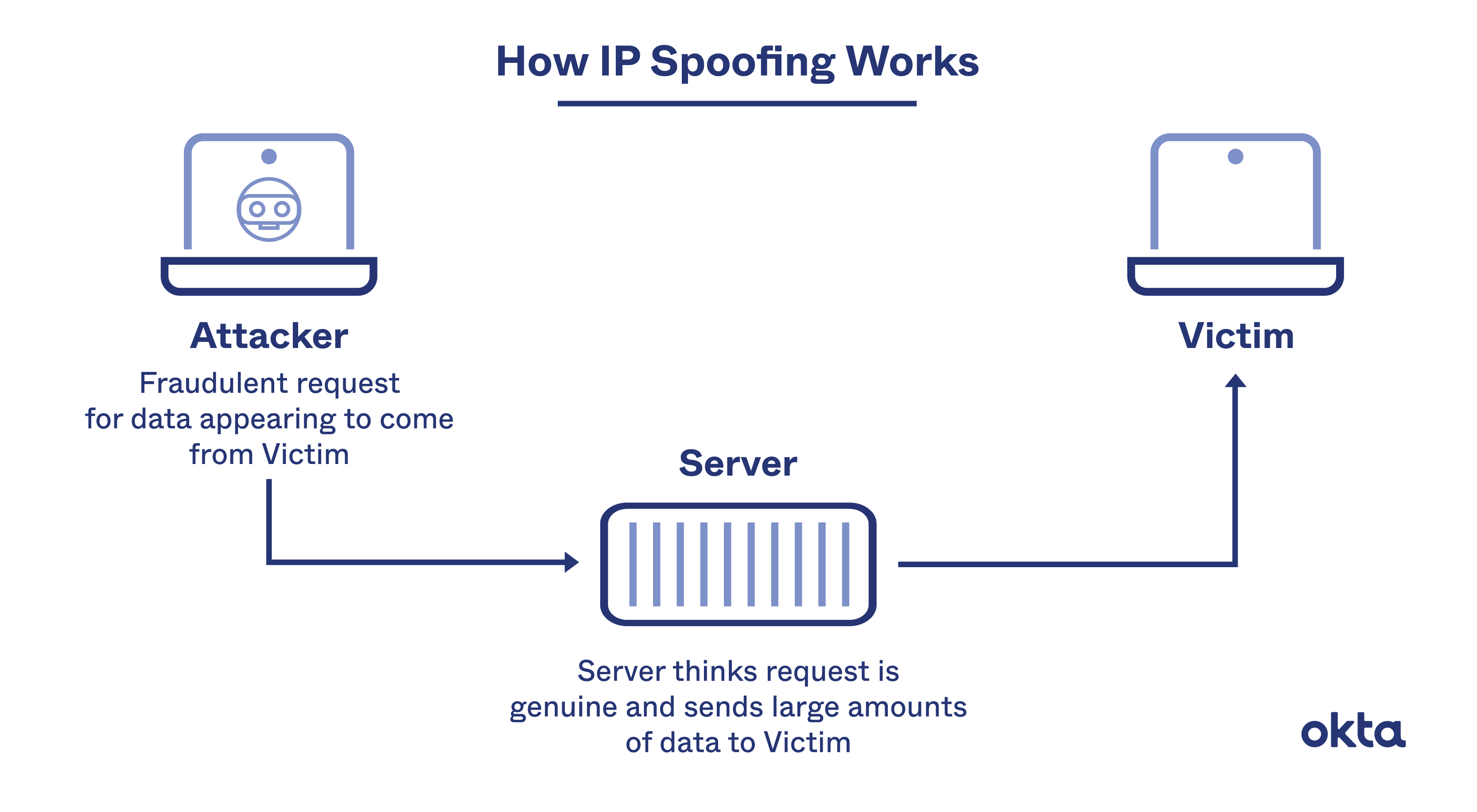
IP Spoofing
Firewalls generally screen network traffic by considering IP addresses (such as 192.168.10.2). Typically, the computers situated behind the firewall enjoy more operational privileges than those on the untrusted periphery of the network. Intruders can manipulate their traffic by using IP addresses that create the illusion of originating from within the firewall, thus obtaining greater access than would typically be allowed.
Malformed Network Packets
Many computers exhibit an excess of politeness. When
presented with an improperly
formatted network packet, they may either attempt to reconstruct it (potentially allowing it to
bypass a firewall or malware analyzer) or reject it and await retransmission. Users of Windows
PCs are familiar with the extended time it takes to install software. Intruders leveraging this
type of attack are either aiming to bypass a specific security measure or initiating a
denial-of-service attack by inducing a prolonged wait, causing the PC to disregard legitimate
transmissions.
Some of these attacks require technical sophistication and the expertise of an experienced
intruder. Worms and Trojan horses are increasingly automating external attacks, scouring the
Internet for vulnerable machines. Compromised machines often serve as a launching pad for
subsequent assaults on new targets. Security experts anticipate a rise in both manual and
automated decryption in the coming years until the Internet attains a higher level of security.
In conclusion, the landscape of cyber threats encompasses a variety of sophisticated attacks
that exploit vulnerabilities in computer systems and networks. Firewall attacks are considered bad because
they undermine the fundamental principles of cybersecurity, leading to unauthorized access, data
breaches, disruption of services, and other detrimental consequences. Protecting against these
attacks is essential to maintaining the integrity, confidentiality, and availability of computer
systems and networks.
The Challenge
Mark module as complete:

Great Job!
Why not check out some other modules?